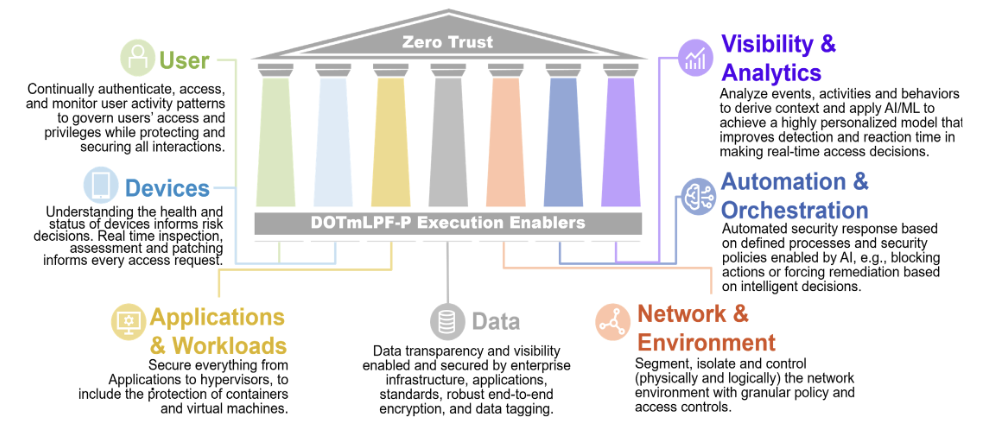
Although the term "Zero-Trust" is commonly used, its definition is not always clear. Zero-Trust It's more than just network access and should be implemented across all aspects of the organization, including data, applications, and automation, to maximize its effectiveness.
According to TechTarget, the Zero-Trust cybersecurity model is: “a cybersecurity approach that denies access to an enterprise's digital resources by default and grants authenticated users and devices tailored, siloed access to only the applications, data, services and systems they need to do their jobs.”
The Zero-Trust model operates off the assumption that all users, devices and networks are untrustworthy and therefore need to be verified before being granted access to network resources. This is different from more traditional security models in which access to internal resources is granted based on a user's physical location or device type, and, once access is granted, the user is trusted for the duration of their session. With a "never trust, always verify” principle, access to resources is only granted following the verification of a number of factors - device security, user authentication, and network context, to name a few. This helps prevent unauthorized access to sensitive data and reduces the risk of cyberattacks.
Given the increasing sophistication of cyberattacks, Zero Trust is needed to protect enterprises against potential dangers. The traditional security solutions that assume a user can be trusted once they’ve gotten inside the network are no longer sufficient to protect organizations against today's threats. The expanding attack surface, BYOD work structures, remote workforce all add to the growing need for better protection.
Zero-Trust & The US DoD
-
Zero Trust Cultural Adoption – All DoD personnel are aware, understand, are trained, and committed to a Zero Trust mindset and culture and support integration of ZT.
-
DoD information Systems Secured and Defended – Cybersecurity practices incorporate and operationalize Zero Trust in new and legacy systems.
-
Technology Acceleration – Technologies deploy at a pace equal to or exceeding industry advancements.
-
Zero Trust Enablement – Department- and Component-level processes, policies, and funding are synchronized with Zero Trust principles and approaches.
Implementing Zero Trust will be a continuous process in the face of evolving adversary threats and new technologies. Additional Zero Trust enhancements will be incorporated in subsequent years as technology changes and our Nation's adversaries evolve.
The Zero-Trust Enterprise Browser
Unlike consumer browsers – which by default have become the OS of most organizations, secure enterprise browsers have been designed for the enterprise. The secure enterprise browser includes security features focused on corporate data, assets, and applications – on prem, hybrid, or SaaS.
In the context of Zero Trust, an enterprise browser plays an important role in helping organizations achieve their security goals by including features such as website restrictions, data leakage protection, and device security, as well as centralized management and monitoring capabilities.
A secure enterprise browser provides comprehensive Zero-Trust control, easily and quickly extended over devices - both managed and unmanaged, users, applications, and data, not just access.
Achieving Zero Trust using an enterprise browser requires several key steps:
-
Content Encryption: To achieve Zero Trust, it's essential to encrypt all sensitive data, whether in transit or at rest. An enterprise browser with built-in encryption capabilities can help to ensure that all data is encrypted and protected from unauthorized access.
-
Robust Security Features: An enterprise browser should have robust security features that focus on corporate data, assets, and applications. This includes website restrictions, data leakage protection, and device security, as well as centralized management and monitoring capabilities.
-
Use Case: To achieve the use case for Zero Trust, it's essential to identify the specific controls required. This includes identifying the applications, data, and services that need to be protected, as well as the devices and users that require access to them.
-
Third-Party Controls: To achieve Zero Trust, it's essential to have controls in place to manage and control third-party access to the organization's resources. This includes controls such as data leakage prevention (DLP), file encryption, and restrictions on downloading data to personal devices or copying and pasting to private email accounts.
An enterprise browser like SURF can help organizations achieve Zero Trust by providing comprehensive control over devices, users, applications, and data, not just access. With robust security features and built-in encryption capabilities, an enterprise browser can help organizations better control employee access to the web and prevent data breaches, all while ensuring that web-based activities are conducted in a secure and controlled manner.
As a matter of fact, the goal of the US DoD when it comes to Zero-Trust is in parallel with the approach delivered by a Zero-Trust, Identity-first secure enterprise browser. It’s a framework to reduce the attack surface, strengthen risk management, and enable effective - but secure - data sharing - all while being able to quickly contain and remediate cyber threats.
Book a Demo