Welcome to the digital age, where data reigns supreme, and safeguarding it is more critical than ever. For companies entrusted with sensitive information, compliance with industry frameworks isn't just a choice—it's a necessity. One such indispensable framework is SOC 2, crafted to ensure the confidentiality, integrity, and availability of customer data. In this blog post, we'll dive into the vital realm of SOC 2 compliance and explore how SURF, with its robust capabilities, can be your ally in navigating the complex waters of security and compliance. Let's uncover how SURF can help you achieve SOC 2 compliance and make your journey smoother.
The Imperative of SOC 2 Compliance
As businesses increasingly leverage technology to manage and process customer data, the need for a standardized framework to ensure the secure handling of this information becomes apparent. SOC 2, developed by the American Institute of CPAs (AICPA), specifically addresses the unique challenges faced by service organizations handling client data in the cloud.
SOC 2 compliance is not merely a checkbox; it's a commitment to meeting stringent criteria encompassing security, availability, processing integrity, confidentiality, and privacy. Achieving SOC 2 compliance not only fortifies an organization's security posture but also builds trust with clients, partners, and regulators.
SURF Zero Trust Browser: A Trusted Navigator in Security
Navigating the intricate waters of SOC 2 compliance requires a robust security solution that aligns seamlessly with the framework's principles. SURF Zero Trust Browser—designed to not just meet but exceed the security expectations outlined in SOC 2.
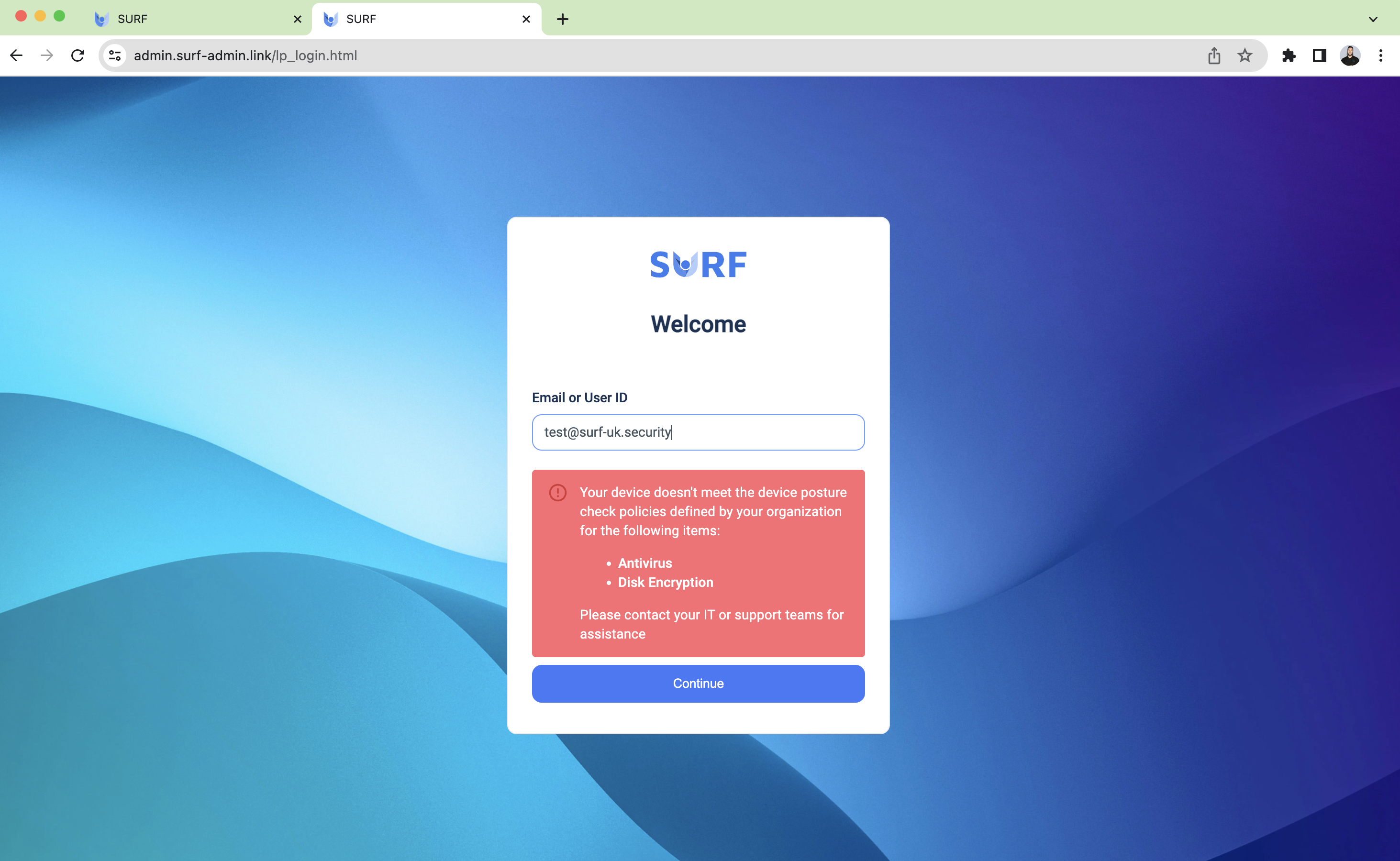
Access Control and device posture checks:
- SURF enforces strict access controls to ensure that users only have the necessary privileges. Upon user login, device posture checks are performed, and if the user's device is not in compliance with the company's requirements (such as having antivirus software running or disk encryption and more), the user will not be granted access. However, if the device is compliant, distinct policies are implemented based on the user's specific level of privilege. This seamless alignment perfectly aligns with SOC 2's emphasis on effectively controlling access to sensitive information.
Encryption, Malware Protection and isolation:
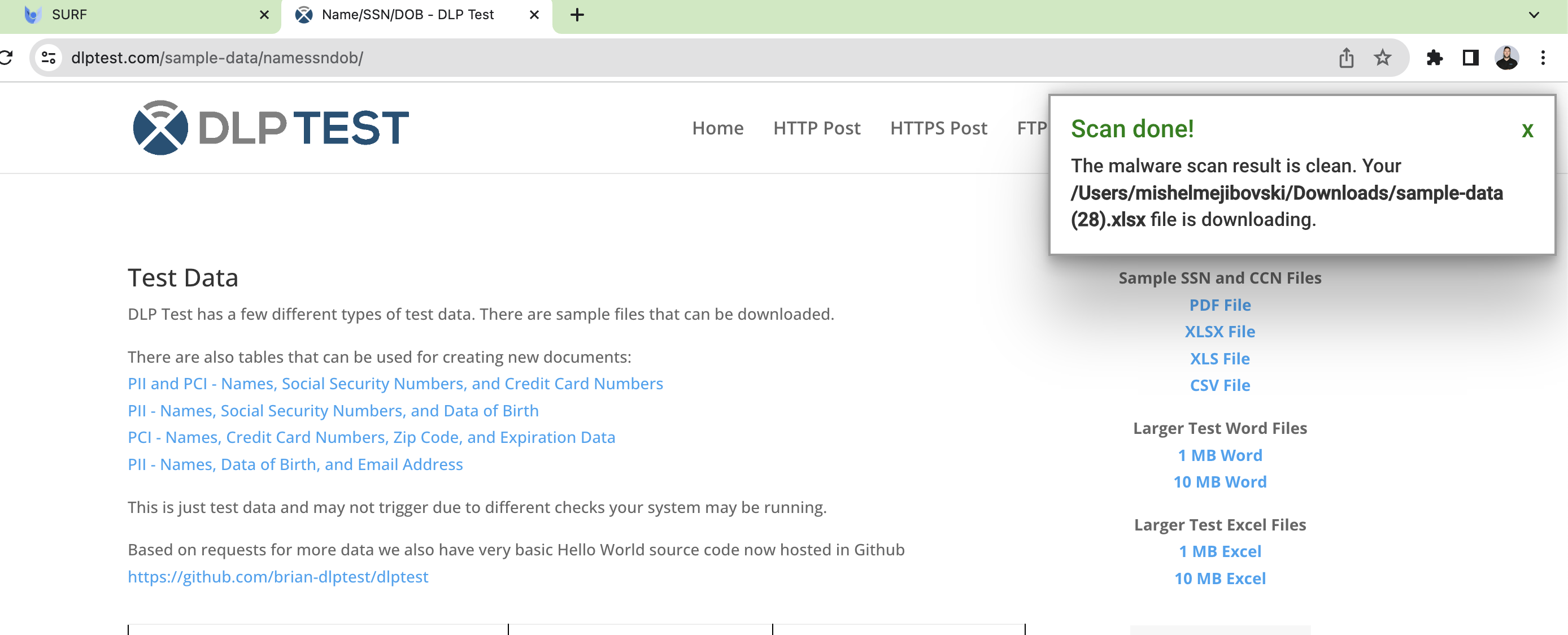
- SURF sets itself apart from standard browsers by providing an additional layer of security. Its built-in isolation feature scans every element and URL that enters its engine, guaranteeing that they are free from malware before allowing them to be downloaded to the endpoint. This unique capability effectively safeguards data through robust security measures, including encryption, malware scanning, and DLP controls, to prevent unauthorized copying and unnecessary transfers. By implementing these measures, SURF aligns with the criteria outlined in SOC 2, ensuring data protection and compliance against malicious software.
Phishing Protection and Web Filtering:
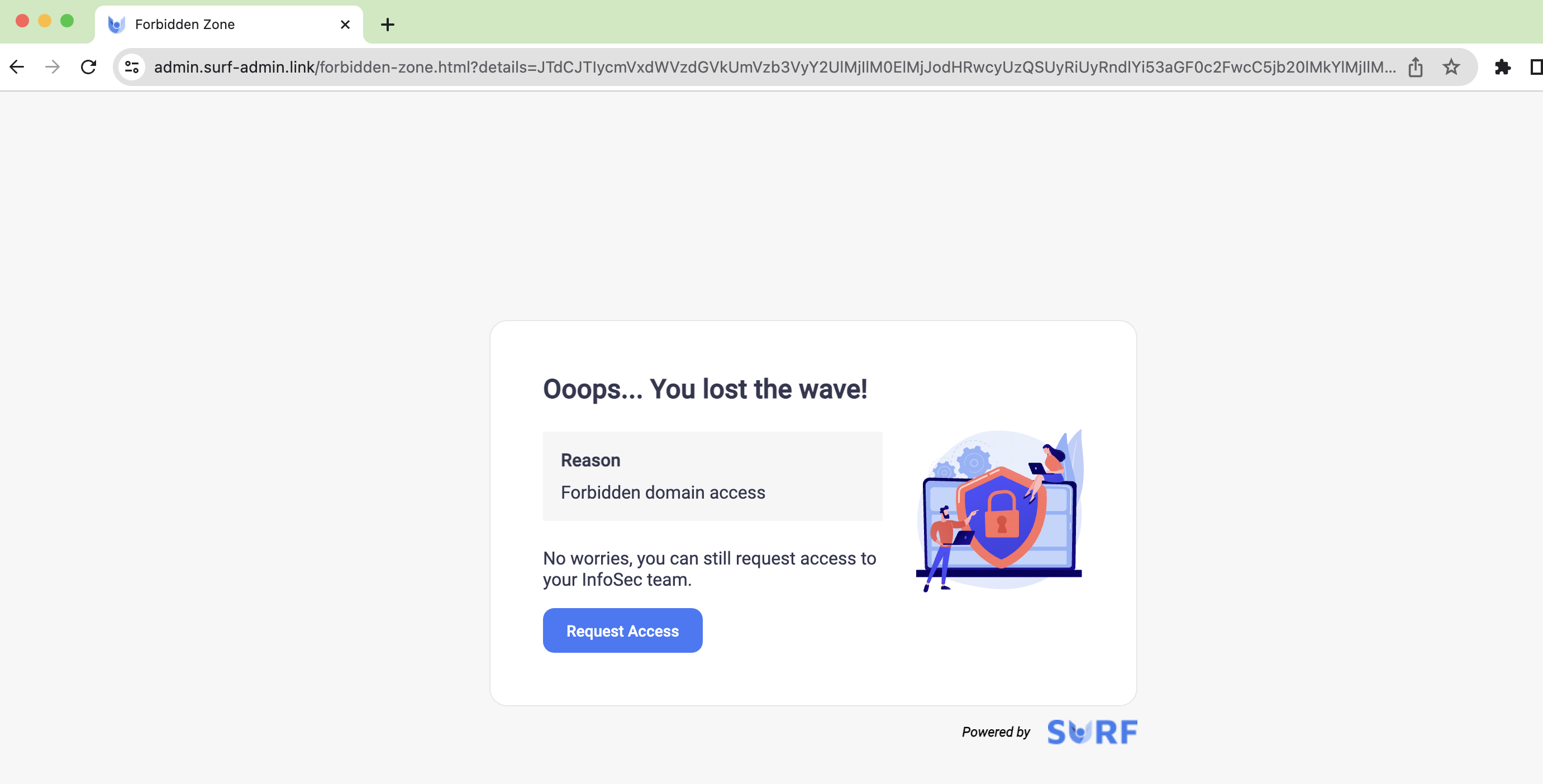
- SURF enhances security measures against social engineering attacks and unauthorized website access through advanced phishing detection and web filtering policies. It not only performs category-based filtering but also allows manual configuration to allow or block specific domains. Additionally, SURF has the capability to block pages when a user enters a specific regex, effectively addressing SOC 2 controls.
Strong Authentication Policies and conditional access:
- SURF seamlessly enforces its own multi-factor authentication or integrates with strong authentication methods and identity providers, guaranteeing that only authorized individuals can access sensitive data. This includes the ability to prompt for a transactional MFA on specific pages within a domain. SURF establishes a conditional access policy, defining itself as the exclusive browser for accessing any sensitive data within the company. By doing so, it ensures that work progresses within the compliance framework, providing an extra layer of security and peace of mind.
Monitoring, Auditing:
The importance of monitoring and auditing cannot be overstated when it comes to achieving SOC 2 compliance, and SURF truly excels in delivering robust monitoring and auditing capabilities. With SURF, you can actively monitor user behavior on your corporate protected applications, effectively preventing the insertion of sensitive information and blocking the upload of sensitive files to specific applications. SURF can capture the screen while alerts occur and swiftly providing them to the SOC team for further analysis. Additionally, SURF allows you to monitor and track user behavior on defined pages, generating detailed anomaly reports and logging any alerts that breach your organizational policy. With this comprehensive suite of monitoring and auditing features, SURF ensures continuous oversight and effective risk mitigation—making it an absolutely crucial aspect of SOC 2 compliance.
Choose SURF, Sail Securely
In the journey towards SOC 2 compliance, organizations need more than just a browser; they need a partner that understands the intricacies of modern security challenges. SURF Zero Trust Browser not only understands but excels in meeting these challenges head-on. Secure your data, bolster your defenses, and navigate the seas of compliance confidently—choose SURF and sail towards security excellence.
Book A Demo