Browser-in-the-Browser (BitB) attacks are a type of phishing attack where the attacker creates a fake browser window within a legitimate browser window to deceive the user.
Here's a step-by-step explanation of how a BitB attack works:
-
Luring the user: The attacker tricks the user into visiting a malicious or compromised website that hosts the phishing page.
-
Creating a simulated browser window: The phishing page uses JavaScript code to create a pop-up window that mimics the appearance and behavior of a legitimate browser window. This simulated window is designed to deceive the user into thinking that they are interacting with a genuine website.
-
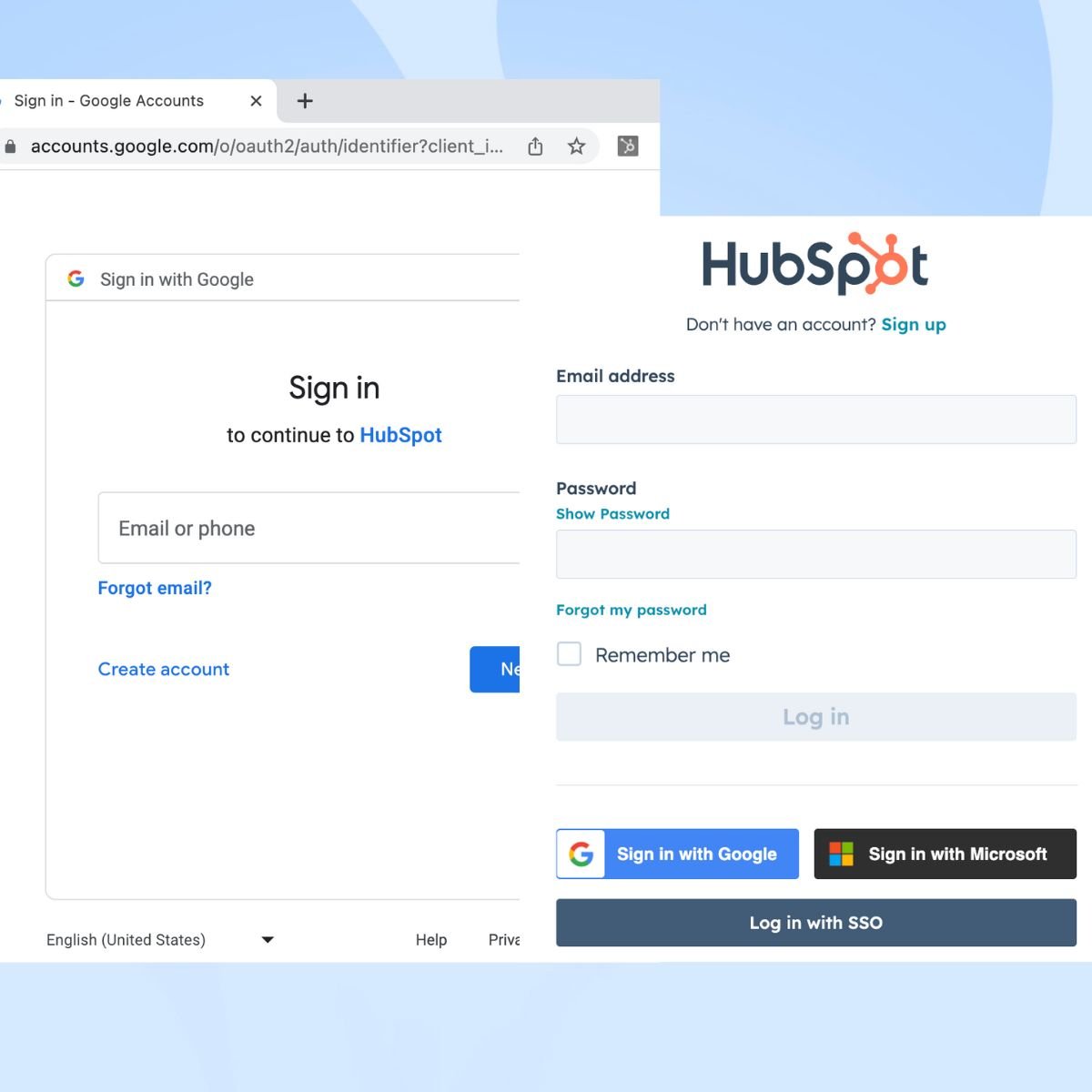
Displaying a fake login form: Within the simulated browser window, a fake login form is displayed. The form is designed to resemble the login page of a popular service that the user may want to access, such as Google or Microsoft.
-
Manipulating the URL and security indicators: The attacker can modify the simulated address bar of the pop-up window using JavaScript code. This allows them to display a fake URL that matches the legitimate service's login page, such as "https://accounts.google.com." The user may not realize that the URL is not actually loaded in the pop-up window but is only shown as an image or text. Additionally, the fake browser window may lack SSL certificates or other security indicators typically present in a genuine browser window.
-
Stealing user credentials: If the user falls for the deception and enters their login credentials into the fake login form, the information is sent to the attacker's server via an AJAX request or a hidden form submission. The attacker then has access to the user's credentials, which they can use to compromise the user's account, engage in identity theft, or launch further attacks.
Real-world examples of BitB attacks have been observed. One notable case involved the targeting of Steam credentials, where attackers created a fake login page with convincing elements, such as a fake green lock sign, a URL field that could be copied, and even an additional window for two-factor authentication. The attackers managed to steal valuable Steam accounts in these campaigns.
The BitB attack is a sophisticated and dangerous phishing technique that can bypass many traditional security measures and deceive even vigilant users. However, there are some steps that users can take to protect themselves from this attack:
-
Exercise caution and be skeptical: Be wary of clicking on links or visiting websites from unknown or suspicious sources.
-
Verify website authenticity: Pay attention to the details of the pop-up window, such as the size, position, appearance, and behavior of the elements. Fake browser windows may have inconsistencies or discrepancies in their look and feel compared to legitimate ones.
- Verifying the authenticity of a website by checking the URL, SSL certificates, and security indicators. Avoid entering sensitive information, such as login credentials, on websites that seem suspicious or untrustworthy.
-
Keep your browser and software up to date: Regularly update your browser to the latest version. Browser updates often include security patches and enhancements that can help protect against known vulnerabilities, including those exploited by BitB attacks. Enable automatic updates whenever possible.
-
Enable two-factor authentication (2FA): Enable 2FA for all your critical online services whenever it's available. Two-factor authentication adds an extra layer of security by requiring a second form of verification.
-
Educate yourself and stay informed: Stay updated on the latest phishing techniques and cybersecurity threats. Regularly educate yourself about common phishing indicators, red flags, and best practices for staying safe online.
Protect your organization from BITB attack with SURF
-
Applying phishing protection: Since the login page/form used in BitB attacks is not hosted by the legitimate domain, SURF is blocking input of the end user corporate credentials to the fake login page. This mechanism helps identify and block such phishing attempts.
-
Phishing protection and frame detection: SURF's phishing protection includes the ability to whitelist specific domains for user logins. If a user tries to login to a non-whitelisted domain, the protection system blocks it. Additionally, SURF renders each frame separately, allowing it to detect and mitigate frame spoofing attempts.
-
Domain age check: SURF has domain age checks enabled, which can help identify suspicious or newly created domains that may be involved in BitB attacks. This check is applied to every frame, providing a comprehensive approach to protection.
-
Restricting access to trusted Certificate Authorities (CAs): SURF allows the restriction of access to trusted CAs only. This means that any attempt to inject a reverse proxy approach, which may be used in BitB attacks, would be blocked if the CA is not trusted.
-
Blocking known phishing sites: SURF's Zero Trust browser protection includes the ability to block known phishing sites, typo-squatting domains, zero-day phishing attempts, and suspected phishing sites. This is achieved through Web Security policies configured to block such categories. By enabling categories related to phishing, you can enhance your protection against BitB attacks.
- Reputation-based checks: SURF incorporates reputation-based checks for every frame, helping identify and block frames associated with malicious or suspicious activities.